SeaSP Community Edition Wordpress Plugin - Rating, Reviews, Demo & Download
Plugin Description
SeaSP Community Edition is an automated Content Security Policy Manager. SeaSP allows you to create, configure, manage, and deploy a Content Security Policy for your site.
The WordPress SeaSP Community Edition plugin catalogs the domains that appear on your site. Categorize and filter out unwanted domains. Add a layer of WordPress security site from Magecart and other cross-site scripting attacks to keep your WordPress site safe.
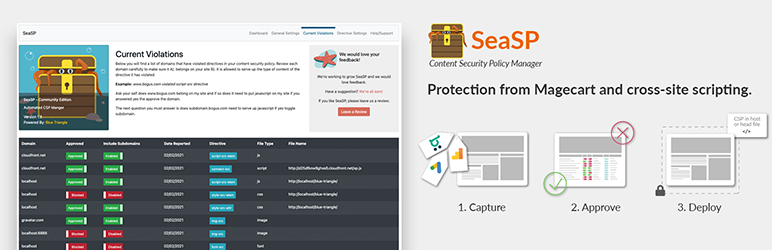
SeaSP installs a strict non-blocking CSP to collect violation data and provide a violation report. Violation data flows into the WordPress database as a PHP option within the plugin options schema. Violations can be approved by domains and categorized by directives (CSS, fonts, images, JS, etc.). You can also approve base domains and subdomains. The SeaSP UI helps users by explaining what each directive does, and how to use them to create a CSP.
After configuring the domain and directive settings switch the CSP to blocking mode. Once the CSP goes into blocking mode, the site’s protected from any unrecognized code. SeaSP Community Edition helps secure your site.
Upgrade Notice for 1.4 only
- When you install this version you will need to rebuild your CSP
Usage
Once installed, a strict non-blocking report-only CSP is implemented on your site. Visit each page of your site to collect CSP violations.
Visit the Current Violations page of the plugin to review domains that have violated a directive in the CSP.
Review each of the domains carefully and check for misspellings of common domains like adobee.com instead of adobe.com as this is a common way hackers inject content into your site.
If you feel confident that the domain belongs on your site and it should be serving the file type stated, click the toggle to approve the domain to include it in the CSP.
If you want to allow subdomains of that domain to be able to serve that type of content, click the Manage subdomains button to view the subdomains.
After this process, you might still see CSP violations regarding inline scripts, inline styles, blobs, or data.
To allow these this type of content in the community version you must navigate to the Directive Settings page, find the offending directive, then toggle the appropriate option.
For convenience, each option has a tooltip explaining what it allows in your CSP.
Walk Through
A walk through video can be found on YouTube here.
Contributing
Pull requests are welcome. For major changes, please open an issue first to discuss what you would like to change.
This project has been tested on WordPress up to version 5.8 on both single and multi-site instances.
The project can be found on github.
This project is sponsored by Blue Triangle.
Third Party Libraries
We use Bootstrap for the UI of our plugin to make the interface clean and simple.
Bootstraps license can be found here
We use bootstrap toggle because simple check boxes can be confusing and we wanted our CSP mangers UI to feel easy. This code was developed for The New York Times by Min Hur and is licensed under MIT
License
Opt In usage data collection
As of version 1.5 users will be able to opt-in for data collection to help us determine how many people are using our plugin and what features we should be working on in future version. This can be managed in the Usage Data Settings page. We collect and send the following data:
1. wordpress version
2. wordpress debug mode
3. wordpress multisite
4. the base url that the plugin is on ex; www.bluetriangle.com
This data is only accessible to the Blue Triangle organization and will be used to determine our user base and feature planning.
Screenshots

Current Violations page is where you review all the domains that have violated your CSP to add them to the policy for the given directive

Directive Settings page is where you set source settings for each directive of your policy



